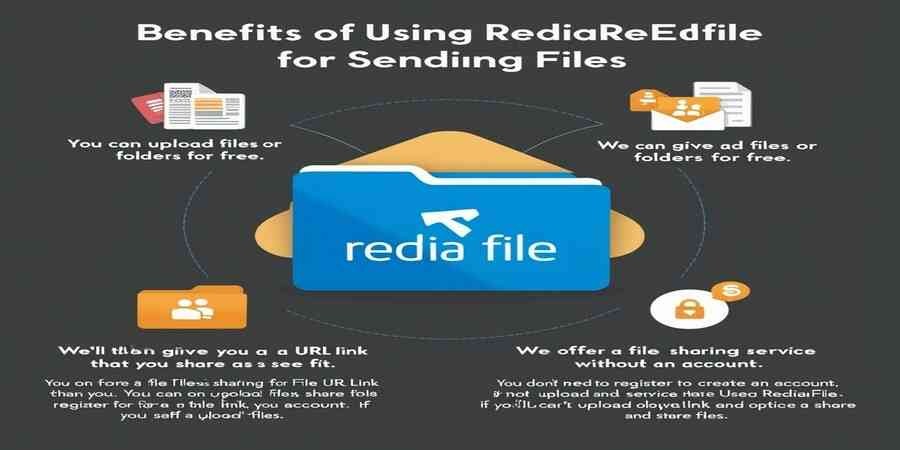
The fix? Strong storage and quick file moves. These let your remote group work as one. Create shared spaces where ideas flow without roadblocks.
Rediafile Business Cloud Storage changes that. It offers a simple way to handle files in the cloud.
Embrace the future of cloud computing with RediaFile, the innovative solution designed to simplify multi-cloud management.
Choosing between Rediafile and Google Drive? Our guide compares pricing, security, collaboration, and features to help you select the ideal cloud stor...
Direct download links, facilitated by platforms like Rediafile.com, offer a powerful and efficient way to share files.
Popular articles
Dec 02, 2024 12:41 PM

Dec 27, 2024 04:42 PM
Nov 25, 2024 08:02 PM

Dec 03, 2024 11:08 AM

Nov 25, 2024 08:21 PM
Categories